This page provides you a detailed approach to configure Kerberos delegation. It also provides details of configurable parameters, prerequisites, and troubleshooting.
Recommended approach
If you are running against Analysis Services (tabular or multidimensional), there are other ways to set up Kerberos Delegation. These options don't require Kerberos Delegation to be set up. To use this approach, the server connection would be made using the Application Pool user and make use of the EffectiveUser connection property to impersonate the Anaplan XLWeb user within Analysis Services itself.
To do this, you need to ensure the Application Pool is running as a domain account and that account has Administrator access on the server. Then set these application settings in the Anaplan XL web.config:
<add key="StopImpersonatingDuringDataAccess" value="true"/>
<add key="StopImpersonatingDuringRelationalDataAccess" value="true"/>
<add key="ForceAnalysisServicesUser" value="true"/>
The first setting makes sure the application pool user is used for the data connection. The second setting makes the EffectiveUser be set to the AnaplanXLWeb user.
Additionally, update this file:
\inetpub\wwwroot\xlcubedweb\bin\xlcubed.data.analysisservices.xml
Ensure the setting enforceuseridentity is set to false:
<connections keepopen="False" keepsession="True" usenativecom="True" useconnectionpooling="False" enforceuseridentity="False" />
Depending on your network setup, the application pool and SQL Server Analysis service users may need to log in. They'll need to be added to the Windows Authorization Access Group built-in Domain group.
Kerberos delegation
If Anaplan XL Reporting Web is installed on a different server than the database, you will need to set up delegation. The Website must be set up to use Windows Authentication.
If you have this type of setup and Delegation isn't configured, then you will receive a message such as "Server is unavailable" for Analysis Services or a "(null) user" error for SQL Server when trying to access published reports.
Most corporations have a standard setup for Delegation, and the Domain Administrators would handle this. This is a guide to how to configure Delegation in the simplest case but is by no means a best practice guide as each domain setup and infrastructure can vary enormously.
There are also many other things that can affect how Delegation works well. These include the network, client security settings, and software. The guide will assume that all clients will use Internet Explorer. There's only one domain and everything is on the same network. There are no firewalls or routers that could block Delegation requests.
Preparation
Before starting, make sure AnaplanXLWeb is working well. This includes loading a report. If it doesn't work, the server won't be available.
Ensure the Anaplan XL Website Application pool is running as either NetworkService or a specifically created domain user and then only "Windows Authentication" and "ASP.net Impersonation" are enabled in the Authentication settings of the website.
Check/clear any existing SPNs for the servers — if any already exist and they're invalid, then the configuration won't work.
Information required
Before configuring Delegation, you will need to know:
| Information | Value |
| What the network domain name is, as this is needed to get a server's Fully Qualified Domain Name (FQDN) | server.domain |
| The name and FQDN of the Web Server | Webserver |
| The name and FQDN of the Analysis Services | ASServer |
| The name and FQDN of the SQL Server (if allowing SQL connections. | SQLServer |
| The port on which SQL Server is running, if allowing SQL connections. | |
| The User ID for the Anaplan XL Web website | WebUser |
| The User ID that the Analysis XL Service is running as | ASUser |
| The User ID that the SQL Server service is running as | SQLUser |
User ID format
If the User IDs are domain accounts, then the format needed is: domain\user.
If the service or application pool is set to run under NetworkService, then use the server name: server.
Access required
You will need to be a Domain Administrator to perform all of the configuration steps.
Domain configuration
Enable Server Delegation
The first step is to enable delegation on ALL the machines involved in the process:
- WebServer
- ASServer
- SQLServer
This is a setting for a domain. You can set it up using the Active Directory Users and Computers tool, which is part of the Microsoft Admin Tools Pack. It'd normally be on the Domain Controller.
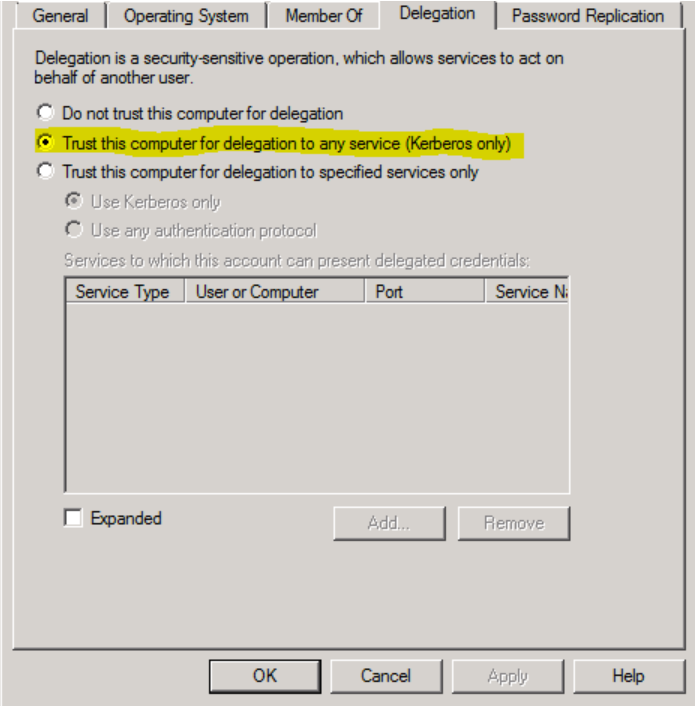
If there is more than one domain controller, then you would need to either start a propagate or wait for this change to be applied to all the domain controllers.
Set SPNs
The Service Principal Names (SPNs) are set using a command-line tool: setspn. This needs to be run in an Administrator Command Prompt with an account that has Domain Admin privileges. It needs to be run for both the server name and the Fully Qualified Domain Name.
If there's more than one domain controller, then you would need to wait for this change to propagate to all the servers. Note that we are using the -S switch, which is available from Windows Server 2008. If you are using a previous version, use the – A switch after manually checking for duplicate SPNs defined in the domain.
Web Server
setspn –S http/WebServer WebUser setspn –S http/WebServerFQDN WebUser
Example:
setspn -S http/webserver domain\appooluser setspn -S http/webserver.domain.com domain\appooluser
Analysis Services
setspn –S MSOLAPSvc.3/ASServer ASUser setspn –S MSOLAPSvc.3/ASServerFQDN ASUser
Named instance
Where InstanceName is the name of the example:
setspn –S MSOLAPSvc.3/ASServer:InstanceName ASUser setspn –S MSOLAPSvc.3/ASServerFQDN:InstanceName ASUser
You may also need to set up an SPN for the SQL Browser Service.
SQL Server
setspn –S MSSQLSvc/SQLServer:1433 SQLUser setspn –S MSSQLSvc/SQLServerDQDN:1433 SQLUser
Where 1433 would be replaced with the proper SQL Server port number
DNS Aliases
If the server has an alias, if the alias is an ANAME alias, you should add the SPNs for the name that users will type in. If it is a CNAME alias, then you must also add the SPNs for the machine name, as the browser may use those when requesting the Kerberos ticket.
User account delegation
Now that the SPNs are set, you need to enable delegation for the service account and application pool users. This is done in Active Directory Users and Computers.
Windows 2012 Server
If you are running Windows 2012 server or higher, you will also need to run the command in PowerShell. You will need to be a domain administrator on the domain controller.
$user1 = Get-ADUser -Identity WebUser Set-ADUser ASUser -PrincipalsAllowedToDelegateToAccount $user1 Set-ADUser SQLUser -PrincipalsAllowedToDelegateToAccount $user1
Please note in this case, you shouldn't include the domain for WebUser, SQLUser, or ASUser.
IIS Configuration
After making changes and running the Delegation setup, run an IISReset before testing and restart Internet Explorer on the client machine.
Check the providers and order
In IIS Manager, right-click Windows Authentication under the authentication section and choose providers. Make sure Negotiate is listed before NTLM. Kerberos may or may not be needed depending on the network setup.
Advanced settings
You may need to disable Enable Kernel-mode authentication. Right-click Windows Authentication under the Authentication and select Advanced Settings. If Delegation doesn't work initially, try toggling this setting (with an IISReset).
With Enable Kernel-mode authentication is disabled, you may face problems publishing from the Excel client, if so, re-enable it.
iOS Access
If you need iPhone/iPad access either via Safari or Anaplan XL Mobile, you need to add a configuration profile to enable single-sign on for the device. This can optionally include a list of application ids. When you register the website in Anaplan XL Mobile, enter the URL, and then leave "Requires Logon" off, authentication will be handled automatically.
To enable SSO, create text file with an extension of .mobileconfig. Copy the following into it and modify as described:
<?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE plist PUBLIC "-//Apple/DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd%22> <plist version="1.0"> <dict> <key>PayloadContent</key> <array> <dict> <key>PayloadDisplayName</key> <string>SSO Settings</string> <key>PayloadType</key> <string>com.apple.sso</string> <key>PayloadVersion</key> <integer>1</integer> <key>PayloadUUID</key> <string>XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX</string> <key>PayloadIdentifier</key> <string>com.YOURCOMPANY.sso</string> <key>Name</key> <string>FluenceXLWeb SSO</string> <key>Kerberos</key> <dict> <key>Realm</key> <string>YOURDOMAIN</string> <key>URLPrefixMatches</key> <array> <string>HTTP://YOURSERVER</string> </array> </dict> </dict> </array> <key>PayloadOrganization</key> <string>YOURCOMPANY</string> <key>PayloadDisplayName</key> <string>Single Sign-On Profile</string> <key>PayloadVersion</key> <integer>1</integer> <key>PayloadUUID</key> <string>YYYYYYYY-YYYY-YYYY-YYYY-YYYYYYYYYYYY</string> <key>PayloadIdentifier</key> <string>com.YOURCOMPANY.sso.profile</string> <key>PayloadDescription</key> <string>Enables Kerberos Authentication</string> <key>PayloadType</key> <string>Configuration</string> </dict> </plist>
In the code sample above, you should replace these values as appropriate:
XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX- Replace with a generated GUID (https://www.guidgenerator.com/online-guid-generator.aspx).YYYYYYYY-YYYY-YYYY-YYYY-YYYYYYYYYYYY- Replace with a generated GUID.YOURCOMPANY- Your company name with no spaces or punctuationYOURDOMAIN- Your FQDN.YOURSERVER- The URL as entered into the web browser/mobile app.
At the same level as the Realm key you can optionally add the following to limit access to Safari/Anaplan XL Mobile:
<key>AppIdentifierMatches</key> <array> <string>com.apple.mobilesafari</string> <string>com.xlcubed.mobile</string> </array>
You can then email the profile to the users. They can then open and install the profile. During the installation process they need to confirm the details and enter a "realm", this would be their own user identification. It can be left blank for them to be prompted for that each time.
Anaplan XL configuration
Anaplan XL doesn't need to do anything. The browser and the different servers handle Delegation before Anaplan XL Web starts processing user requests.
Troubleshooting
Microsoft Kerberos testing tool
Microsoft has a tool available to test that Delegation has been correctly configured. This can be downloaded from the Microsoft site .
Alternate testing tool
There's also a Kerberos website you can install. It needs to be set up to copy the exact configuration and can then be used to check the configuration. It'll also provide options to fix any problems it finds.
Non-IE browsers
Browsers other than Internet Explorer can use Kerberos. Here are some tips to help. If you can't get it working, then you need to use Internet Explorer. You can also set up Dual Authentication for access to remote clients.
Chrome
You would need to add all the servers involved in the process to the allowed server list. This is done by adding command line parameters to a browser shortcut:
"C:\Program Files\Google\Chrome\Application\chrome.exe" --auth-server-whitelist="ASServer,WebServer,SQLServer" --auth-negotiate-delegate-whitelist="ASServer,WebServer,SQLServer"
Or by updating the registry.

