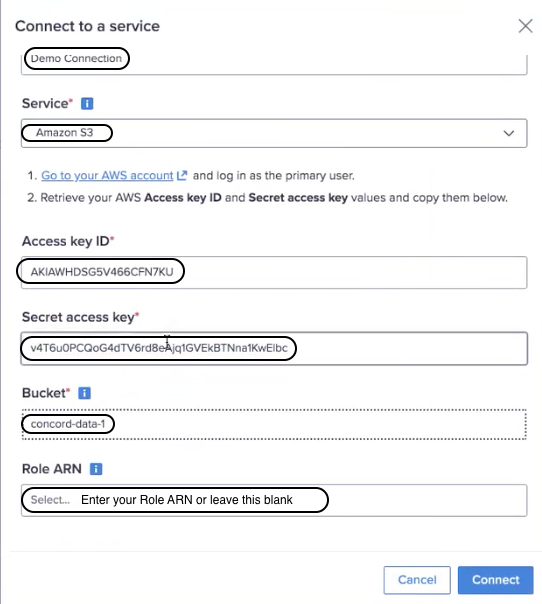
You can restrict bucket access by setting it to a specific IAM role.
To set your bucket for a specific IAM role, follow the configuration steps below.
- Create a new IAM user, if required.
Note: the IAM user can also be from a service account. - Create an IAM Role if you do not already have one.
- Associate the IAM user with IAM Role.
- Create the bucket policy. The policy sets read/write access at the S3 bucket level.
- Associate the IAM Role with bucket policy.
Note: this corresponds to the Role ARN step in Edit a connection. - Generate keys for the IAM user, not the root level. You need both an access key ID and a secret access key.
- As shown in the screenshot below, enter the:
- Access key ID
- Secret access key and
- Role ARN for the IAM user when you create a new connection.